By Aris Medical Solutions
Many medical practices and business associates have the misconception that if they are fined they can simply close their doors and not be obligated to pay the fines or penalties. We have been asked if this will work many times. The Office for Civil Rights (OCR) has answered this haunting question.
Three years ago the OCR received an anonymous complaint against Filefax, Inc. that transported 2,150 patient files to be shredded. These files were left in an unlocked truck in their parking lot, or by granting permission to an unauthorized person to remove the files from Filefax, and leaving the Protected Health Information (PHI) unsecured outside the Filefax facility.
Although Filefax shut their doors during the course of the OCR’s investigation they were still obligated under the law. In 2016, a court in unrelated litigation appointed a receiver to liquidate its assets. In addition to a $100,000 monetary settlement, the receiver has agreed, on behalf of Filefax, to properly store and dispose of remaining medical records found at Filefax’s facility in compliance with HIPAA.
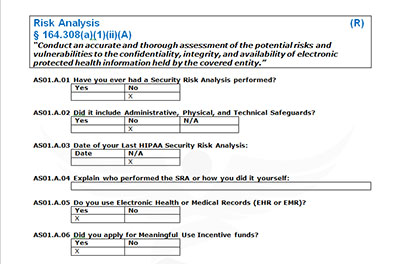
The first step in protecting your practice or business is to conduct a thorough security risk assessment and identify vulnerabilities and workflow. From there you can develop a risk management plan to ensure you document your compliance efforts and mitigate risks.
For more information on how Aris Medical Solutions can help your organization with HIPAA Compliance and Protecting your Data call 877.659.2467 or click here to contact us.
“Protecting Organizations through Partnership, Education, and Support”