When we discuss IT security, we generally think of a company that maintains our computer network. That is partially true, but that is just the beginning. There is a difference between maintaining your network and securing it. There are a lot of companies that are eager to maintain your network because you pay them a monthly fee to do so. Maintaining a network is making sure updates are done, anti-virus / anti-malware are current, upgrading any technology that is outdated or about to be unsupported. A network security company tests to see if there are any open vulnerabilities that could affect or infect your network. There is a huge difference between the two.
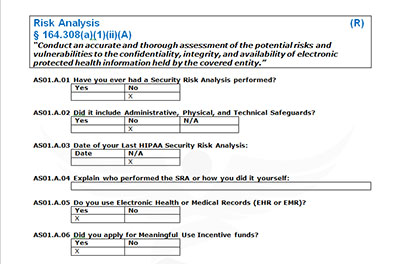
For example, a misconfigured settings of a Windows operating system permitted access to files containing PHI without requiring a username or password. Then two years later a second breach occurred when a server was misconfigured following an IT’s response to troubleshooting an issue, this time it exposed patient information over the internet. These two breaches cost Cottage Health a $3M fine. The Office for Civil Rights (OCR) investigation found that they had not conducted an accurate and thorough assessment and failed to implement security measures sufficient to reduce risks and vulnerabilities to a reasonable and appropriate level based on the size of their organization. Even though they had an IT company maintaining their ePHI system, they failed to obtain a signed business associate agreement.
Another breach that happened in 2014 has just been settled by the OCR. Touchstone Medical Imaging has been ordered to also pay $3M. The OCR and the FBI informed Touchstone in 2014 that one it’s FTP servers allowed uncontrolled access to ePHI. The uncontrolled access permitted search engines to index the patients personal information, which remained visible after the server was taken offline.
Touchtone Medical Imaging fined $3M
The lesson here is, what you do today can affect your business in the years to come. Make sure you are doing what is reasonable and appropriate to safeguard your patient information. One more keep point, these are just the federal fines. All 50 states now have their own set of privacy laws to protect personal identifiable information that doesn’t have anything to do with health information. Since we work in healthcare, we must adhere to state and federal privacy laws. No longer can you ignore the elephant (HIPAA) in the room, HIPAA is here to stay and you need to choose wisely who you work with to secure your data.
If you haven’t conducted an audit this year, now is a good time to schedule one to ensure your data is secure. If you would like more information on network security audits, contact us at 877.659.2467 or complete the contact us form.