Security Incident Procedures 45 CFR § 164.308(a)(6)(i) There must be a policy and procedure in place to identify security threats and record them. Being aware of the type of threats that exist will help you create a workforce that will be diligent in protecting patient data. Most security issues could have been avoided if the staff had understood what a Security Incident was. Making a list of typical security threats would help educate your staff.
Response and Reporting 45 CFR § 164.308(a)(6)(ii) Once you have identified a security incident, you must have a plan in place to mitigate the situation. This is commonly referred to a Breach Notification Plan. Not all security incidents require you to notify the patients, but you must know when to do so. State laws will supersede federal law if the state law is more stringent.
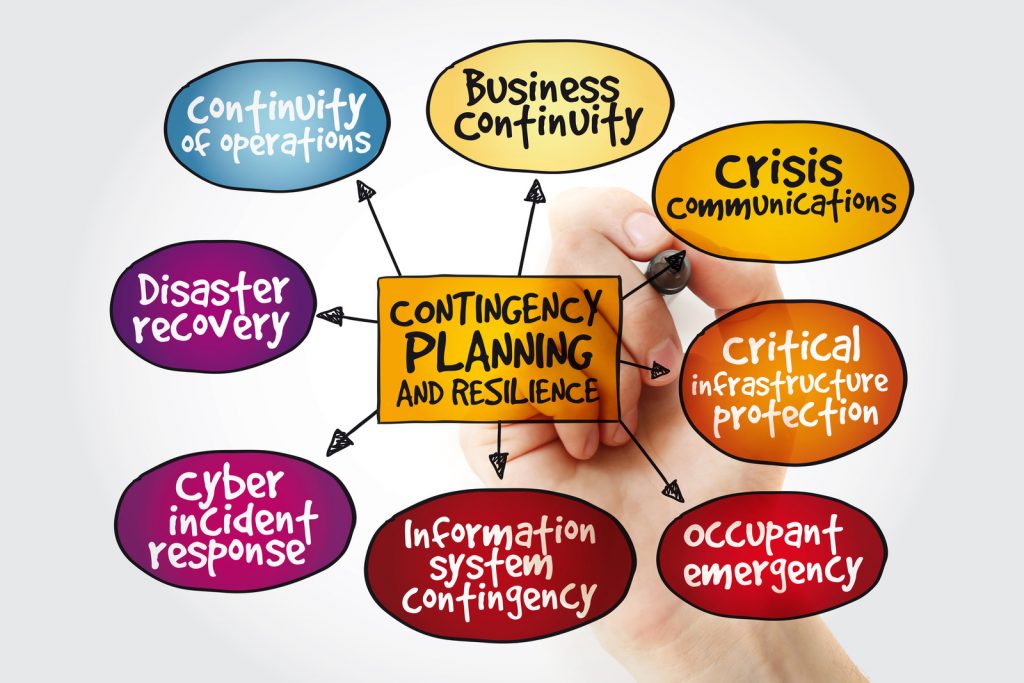
Contingency Plan 45 CFR § 164.308(a)(7)(i) This is one of the most overlooked requirements of the Security Rule. Your organization must create and document a plan on how your organization will protect and restore or have access to your data in case of an emergency. The emergency could something as simple as a power outage or something of a greater magnitude like a natural disaster. Your contingency plan should include the following sections:
Data Backup plan 45 CFR § 164.308(a)(7)(ii)(A)
Disaster Recovery Plan 45 CFR § 164.308(a)(7)(ii)(B)
Emergency Mode Operation Plan 45 CFR § 164.308(a)(7)(ii)(C)
Testing and Revision Procedures 45 CFR § 164.308(a)(7)(ii)(D) Applications and Data Criticality Analysis 45 CFR § 164.308(a)(7)(ii)(E)
Let Aris work with you for an easy online path to HIPAA compliance
