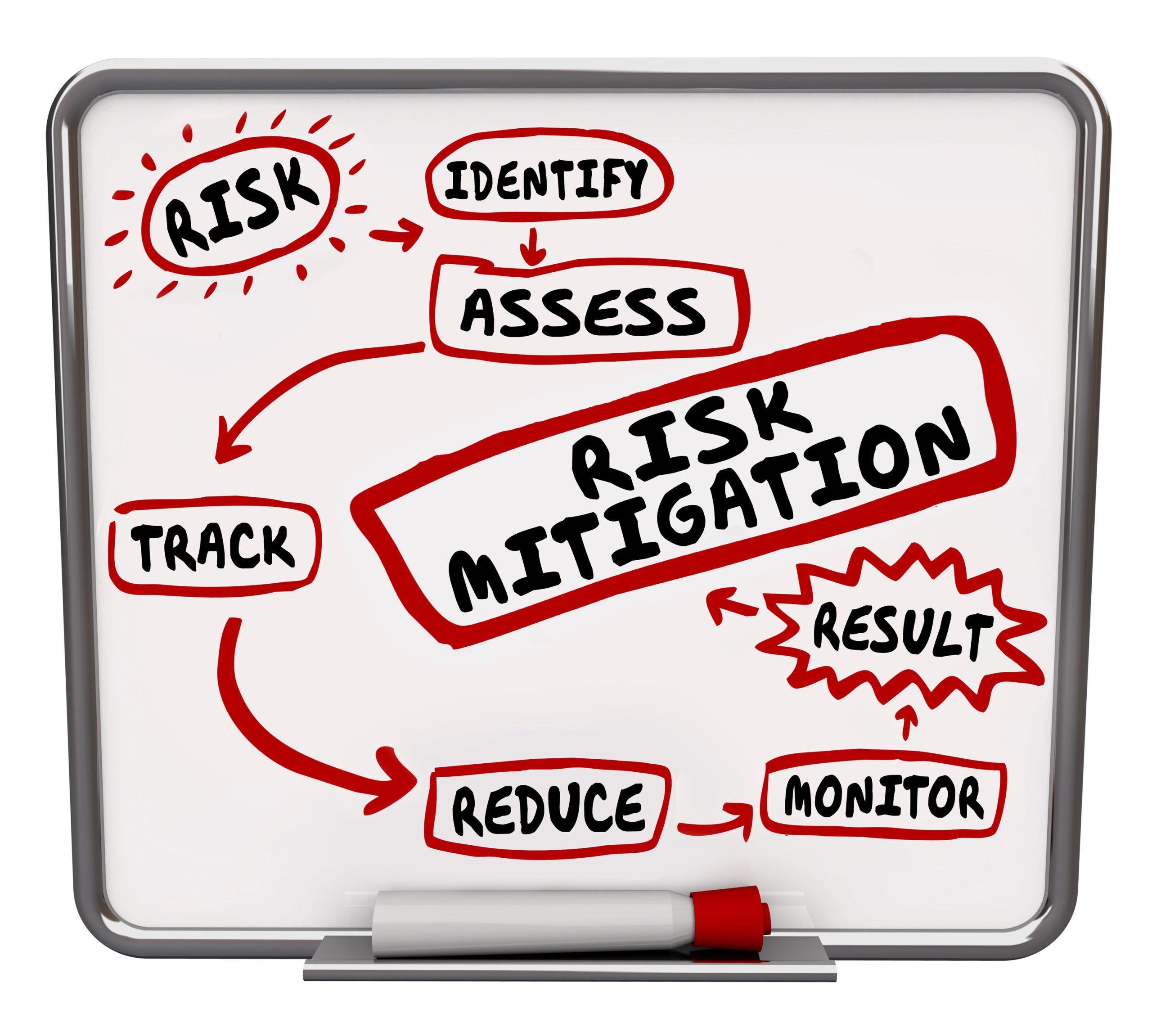
Avoid common misconceptions about HIPAA compliance. Learn the critical steps needed to avoid Chiropractor HIPAA violations and fines. Many chiropractor practices think the Government SRA tool is all they need for their HIPAA risk assessment. Keep in mind, it does not include policies and procedures, therefore you must create your own. Also, many chiropractic practices are members of a group that supply a “HIPAA Binder”. Again, most of these groups do not include policies and procedures. Without proper documentation, a chiropractic practice can be assessed with HIPAA violations and fines.
Another common misconception is that small practices believe they are too small to attract attention from the Office for Civil Rights (OCR). In reality, it takes just one patient complaint, a dissatisfied employee, or a data breach to initiate an audit. Remember, once an investigation begins, the OCR will examine your entire HIPAA compliance program — not just the specific incident in question.
Lastly, many organizations think HIPAA can be a once and done process. This can cost you $$$$$$ in fines! HIPAA requires every organization that is involved with patient data to document their ongoing compliance efforts.
Here are a few examples of Chiropractic practices and some multi-specialty practices that have been fined:
- Arkansas Chiropractic Clinics — $321,000 fine
Two chiropractic clinics in Arkansas were fined a total of $321,000 after improperly disposing of patient records by dumping them in a public park, violating HIPAA’s privacy and secure disposal requirements. - Illinois Chiropractic Offices — Ransomware and data breach incidents
Several chiropractic practices in Illinois experienced ransomware attacks, with ransom demands reaching up to $10,000. While specific OCR fines were not disclosed, these events highlight serious security lapses and the risk of significant penalties. - Stolen devices containing ePHI — $150,000 fine
In a case not exclusive to chiropractic, a healthcare provider failed to update and secure outdated systems, leading to a malware breach and resulting in a the fine from the OCR. - Missing risk analysis — $50,000 fine
Another provider, a clinic using mobile devices like tablets or iPads, was fined $50,000 for failing to conduct a risk analysis and implement appropriate security controls on mobile devices. A critical requirement for chiropractic offices using digital tools.
Privacy & Unauthorized Access Stories
- Receptionist displaying PHI on a tablet
At a chiropractic office, an iPad used for patient check-in accidentally showed other patients’ names and birthdates, resulting in a HIPAA privacy violation. - Chiropractor misusing patient address to send flowers
In Colorado, a chiropractor accessed a patient’s medical record to obtain her address and sent her unsolicited flowers. This was widely viewed as a serious breach of patient privacy and another type of violation of the HIPAA privacy rule.
Ask yourself: How much of your hard-earned revenue are you willing to risk?
Remember, it only takes a single patient complaint or one disgruntled employee to prompt an investigation by the Office for Civil Rights (OCR). Once that happens, every aspect of your compliance program will come under scrutiny.
Ask yourself: Are you confident your documentation can stand up to that level of review? Most practices lack the required policies and documentation.
Are you ready to protect your practice? We are here to help you avoid common misconceptions about HIPAA compliance. Do you have the critical steps needed to avoid Chiropractor HIPAA violations and fines? Our online HIPAA Keeper™ includes all policies and procedures required under HIPAA. We also include patient and HIPAA documentation. When HIPAA rules are updated or added, we update our system to keep you up to date. Also, we are always improving our system to make sure users are aware of new threats and how to protect their organization.
Still not sure? Check out our video that explains our 7-Steps in the HIPAA Keeper™ or Schedule a live demonstration to see for yourself how easy maintaining HIPAA compliance can be!